Exposure management in 2026 is no longer defined by how many assets you can scan. It is defined by where visibility and control still exist when attacks move from discovery to execution.
Most modern attacks do not exploit misconfigurations or unpatched systems. They exploit trust. In fact, according to Statista, the usage of valid credentials is now the joint-top initial access vector globally (30%), tied with software exploitation. In short, Impersonation, credential abuse, and scam-driven access attempts succeed because they unfold during legitimate user interactions, long after traditional exposure tools have done their job.
To understand why account takeover and digital fraud continue to scale, enterprises need to think in layers. Not overlapping products, but distinct exposure layers that activate at different moments in the attack lifecycle.
This challenge is often discussed under the banner of Continuous Threat Exposure Management (CTEM), a security approach focused on continuously identifying, prioritizing, and reducing exposure across an organization’s digital environment.
What is an exposure management stack?
An exposure management stack is a layered security model that maps where risk is visible across infrastructure, external assets, attack execution, and code. Each layer covers a different phase of attacker activity, and no single tool spans them all.
The key distinction is simple. Exposure describes where attackers can operate. Execution describes where attackers actually do operate. Most security stacks are strong in the first category and weak in the second.
Why exposure management fails when attacks execute
Traditional exposure management focuses on inventory, misconfiguration, and reachability. These are necessary foundations, but they assume attacks succeed by finding technical weaknesses.
Modern attacks succeed differently.
Impersonation campaigns, phishing, and credential replay use valid credentials, real applications, and legitimate workflows. There is no vulnerability to scan for. No asset to flag as misconfigured. By the time execution begins, most exposure tools have already gone silent.
This is not a tooling failure. It is a timing gap.
The fundamental mismatch is latency. ASM and EASM rely on scanning cycles, crawling the web or polling APIs to discover new assets. These scans happen on a schedule, whether hourly, daily, or continuous but queued.
Attacks involving human deception operate on interaction time, not scan time. By the time an external scan identifies a malicious domain, the credential submission has already occurred. You cannot solve a real-time interaction problem with a scheduled inventory solution.
This is the same timing gap that limits domain takedown services, which are effective for cleanup but structurally unable to protect users while attacks are active. Read more about this, in our short guide: What Domain Takedown Services Miss & How to Close Gaps.
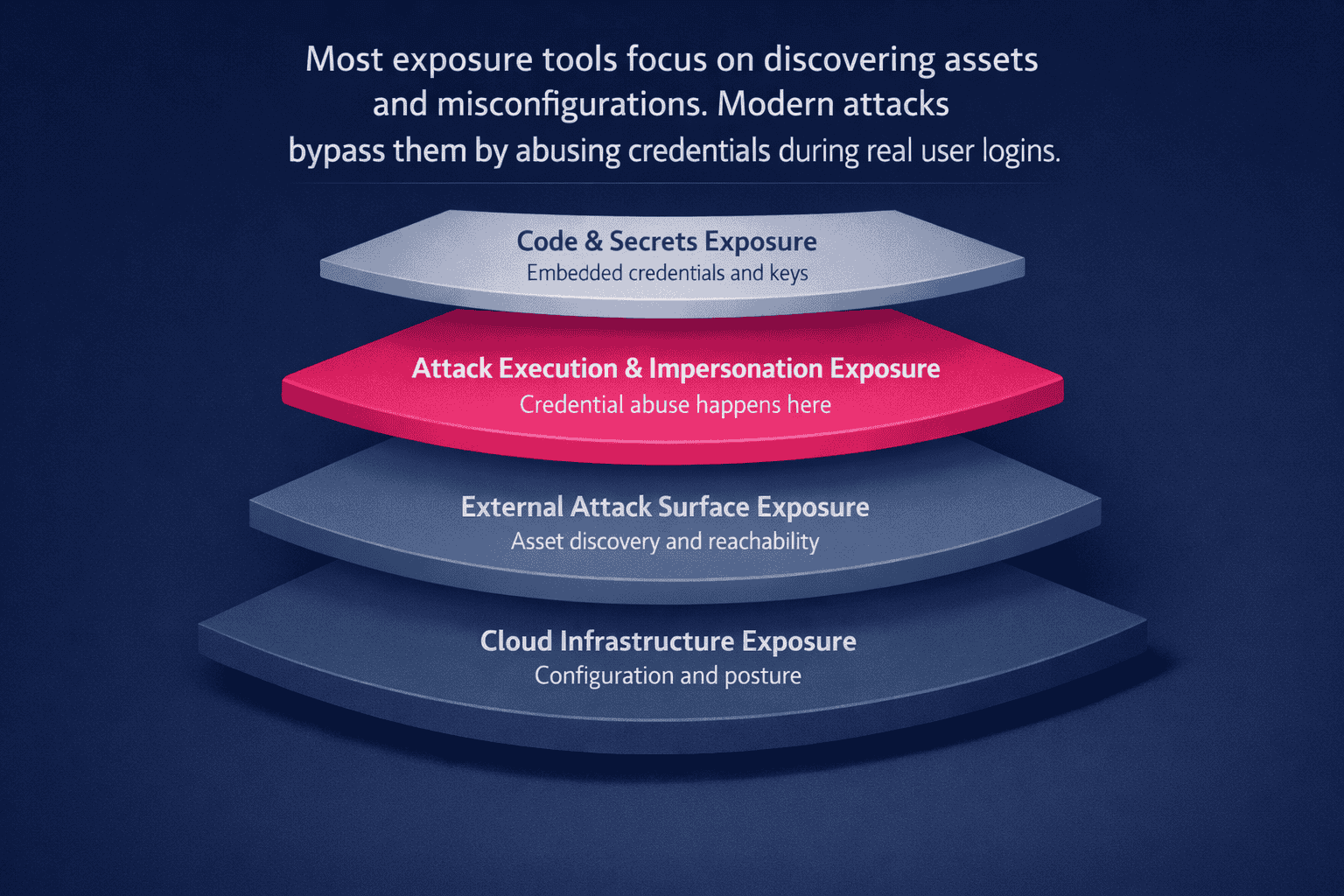
The Four Distinct Layers of Exposure Management
How the Four Exposure Layers Map Across the Attack Lifecycle
| Exposure Layer | Focus Area | What It Covers | Representative Leader |
| Layer 1: Cloud Infrastructure | CNAPP / ASM | Cloud assets, identities, misconfigurations | Wiz |
| Layer 2: External Attack Surface | EASM | Internet-facing assets, shadow infrastructure | Palo Alto Cortex Xpanse |
| Layer 3: Attack Execution & Impersonation | ATO, impersonation, credential abuse | Scam-driven access during authentication | Memcyco |
| Layer 4: Code & Secrets | Secrets hygiene | Credentials in code and pipelines | GitGuardian |
Layer 1: Cloud infrastructure exposure (CNAPP and ASM)
What this layer covers
Cloud infrastructure exposure focuses on internal assets, identities, permissions, and configurations. It answers questions like which workloads are exposed, which roles are over-privileged, and where policy drift exists.
Platforms such as Wiz anchor this layer by providing deep visibility into cloud posture and risk prioritization.
Where it goes blind
This layer does not observe user deception, impersonation, or credential misuse. It does not see attacks that arrive with valid credentials and interact with applications exactly as intended.
Layer 2: External attack surface exposure (EASM)
What this layer covers
External attack surface management focuses on internet-facing assets, shadow infrastructure, forgotten services, and externally reachable entry points.
Solutions like Palo Alto Xpanse help teams discover and monitor assets that attackers might target from the outside.
Where it goes blind
EASM detects assets, not attacks. It cannot see scam execution, impersonation flows, or credential replay attempts that use legitimate applications.
Layer 3: Attack execution and impersonation exposure
This is the missing layer in most exposure strategies.
What this layer observes
Attack execution exposure focuses on impersonation-led access attempts, credential abuse during authentication, and scam-driven interaction with real applications.
This is where phishing campaigns turn into account takeover. Where harvested credentials are replayed. Where trust is abused rather than bypassed.
Why other layers miss this
There is no infrastructure weakness to detect. No anomalous configuration. The attack occurs during normal authentication flows, using real credentials and real users.
Why this layer matters
This is where financial fraud, account takeover, and customer harm actually materialize. Timing, not detection volume, determines whether damage occurs.
Digital impersonation and account takeover protection solutions like Memcyco are designed specifically for this execution-phase gap, providing visibility and protection during impersonation and credential abuse rather than before or after it.
Layer 4: Code and secrets exposure
What this layer covers
Code and secrets exposure focuses on credentials, API keys, and sensitive data embedded in repositories or pipelines.
Platforms like GitGuardian help organizations prevent accidental credential leakage and reduce downstream abuse risk.
Where it stops
This layer does not observe live impersonation, scam execution, or credential replay once credentials are in circulation.
Why no single tool can cover all four layers
Exposure management is not a feature gap problem. It is an architectural one.
Discovery-focused tools cannot observe execution-phase abuse. Execution-phase protection does not replace asset inventory or secrets hygiene. Attempting to collapse all four layers into a single platform creates blind spots rather than eliminating them.
Mature security programs accept this reality and design coverage accordingly.
The Anatomy of a Blind Spot: A Real-World Example
To understand why exposure layers must remain distinct, consider a common localized brand impersonation attack targeting customers.
- The Setup: An attacker registers a lookalike domain and clones the login page. Layer 2, external attack surface exposure, may eventually identify the domain, but often only after the campaign is already active.
- The Lure: Phishing messages are sent to customers. Layer 1, cloud infrastructure exposure, sees nothing. No systems are misconfigured. No infrastructure is touched. Code and secrets exposure is irrelevant.
- The Click: A customer follows the link and lands on the fake page. From the user’s perspective, nothing appears abnormal. The browser behaves as expected.
- The Execution: The customer submits credentials, which are then replayed against the legitimate application. At this moment, only the attack execution layer can recognize that scam-influenced credentials or devices are interacting with the real authentication flow.
The Aftermath: To infrastructure and asset-focused tools, the login appears valid. The breach is complete, even though the exposure stack appeared comprehensive on paper.
Attacks like reverse proxy phishing exploit this exact moment, relaying valid credentials through real authentication flows even when multifactor authentication is enabled.
Read more about this: How to Detect and Stop Reverse Proxy Phishing Attacks in Real-Time.
How security teams should evaluate their exposure stack in 2026
Security leaders should ask:
- Which exposure layers do we cover well today?
- Where do attacks currently bypass visibility?
- At what point does protection meaningfully engage?
- Do we see impersonation and credential abuse as they occur, or only after damage?
These questions reveal gaps far more clearly than feature comparisons.
Beware the all-in-one platform trap
As vendors consolidate, many EASM platforms now claim phishing detection or digital risk protection capabilities. These features often rely on threat intelligence feeds rather than real-time execution signals.
Identifying a malicious domain hours after it appears is useful for takedown workflows, but it does nothing for the customer being scammed in that moment. If a solution cannot identify when scam-influenced credentials or devices reach the legitimate authentication flow, it remains an inventory tool, not a protection layer.
Read more about real-time attack execution signals, and how they help intercept attacks as they’re happening, in our short guide: Account Takeover Detection in Action: The Telemetry Signals You’re Missing
Conclusion: exposure is not where attacks end
Modern attacks do not fail because enterprises lack visibility into assets. They succeed because visibility often ends before execution begins.
Exposure management in 2026 requires acknowledging that impersonation and credential abuse operate in a different layer altogether. Closing that gap is less about adding more scanners and more about engaging at the moment trust is abused.
FAQs
1. Why do traditional ASM and CNAPP tools fail to detect account takeover (ATO)?
Traditional ASM and CNAPP tools focus on infrastructure exposure and configuration risk, not the abuse of legitimate access. Most ATO attacks use valid credentials against real applications, leaving no vulnerability or misconfiguration for discovery-based tools to flag.
The blind spot is structural. These tools operate at discovery and posture layers, while ATO executes later, when stolen credentials interact with real authentication systems.
2. How is exposure management different from attack surface management (ASM)?
Attack surface management focuses on discovering assets, such as servers, domains, and cloud resources. Exposure management is broader. It maps where attackers can operate across the full lifecycle, from discovery through execution.
ASM is one layer within exposure management, but it does not address execution-phase risks such as credential abuse, impersonation, or secrets misuse.
3. Does a CNAPP platform cover the attack execution layer?
No. CNAPP platforms are designed to secure cloud infrastructure, identities, and configurations. They do not provide visibility into impersonation-led access attempts or credential abuse as it reaches real authentication flows.
This is not a limitation of implementation, but of scope. CNAPP tools are essential for cloud security, but they do not operate at the execution layer.
4. What is the execution gap in modern security stacks?
The execution gap is the lack of visibility when attacks move from discovery into live interaction. Many organizations have strong coverage for infrastructure exposure and external assets, but limited ability to detect attacks that use valid credentials against real systems.
As a result, security teams can see the assets involved, but not the attack itself, because it unfolds inside legitimate authentication flows.
5. Why are identity and access tools alone insufficient for preventing scams?
Identity tools verify credentials and enforce authentication policies. They are not designed to determine whether credentials were obtained through impersonation or deception before the login attempt.
When attackers use valid credentials, identity systems correctly authenticate the user. Without execution-phase visibility, the abuse appears indistinguishable from legitimate access.
6. Should security teams consolidate exposure management into a single platform?
Not today. Exposure management spans distinct layers that activate at different stages of an attack. No single platform covers cloud posture, external assets, execution-phase abuse, and code security comprehensively.